Watch CBS News
#Georgia #Tech #drones #enhance #campus #security
Watch CBS News
Georgia Institute of Technology recently became one of the first colleges in the U.S. to roll out a drone program that enhances campus security.
#Georgia #Tech #drones #enhance #campus #security
Samsung may use a new face unlock technology on the Galaxy S27 Ultra, which could rival Apple’s Face ID. According to tipster @SPYGO19726 on Twitter, an early test firmware for the Galaxy S27 Ultra mentions a biometric security framework called “Polar ID v1.0.” Internal logs describe the term as a “polarized-light authentication system.”
Exclusive: Early test firmware for the Galaxy S27 Ultra references something called “Polar ID v1.0” under the biometric security framework. Internal logs describe it as a “polarized-light authentication system”
— S (@SPYGO19726) November 7, 2025
In a follow-up, the tipster notes that the module is tied to the ISOCELL Vizion sensor on the front and a new secure enclave routine. Probably more exciting is the claim that the mechanism works with an unlock latency of around 180 ms. Of course, it also provides improved resistance to spoofing compared to Samsung’s current face unlock.
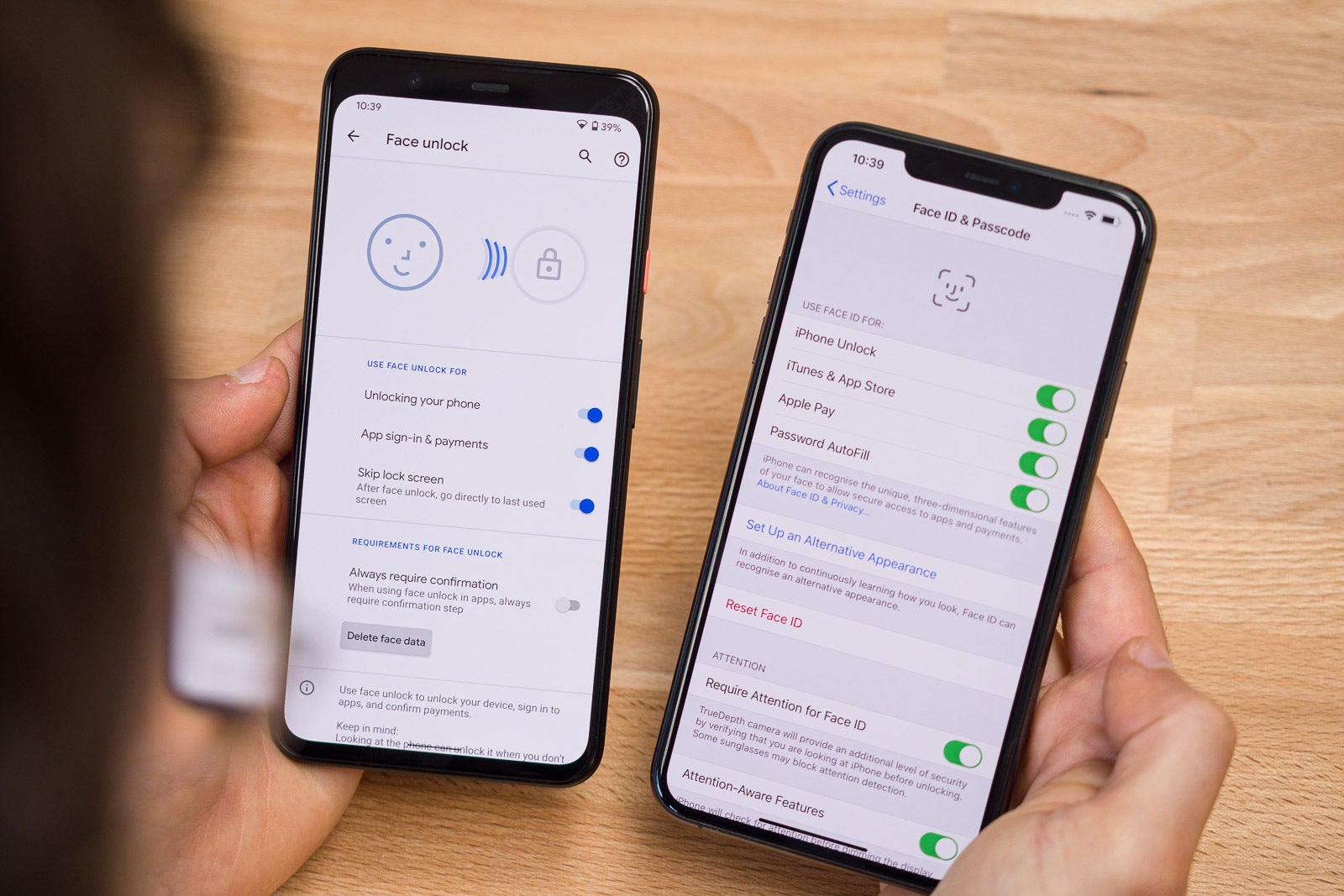

Face unlock features on the Google Pixel 4XL and iPhone 11 Pro Max. | Image credit – PhoneArena
While the source of that rumor has a mixed reputation, a couple of things make that information sound very likely. Firstly, that’s not the first time we’re hearing about Polar ID on a Samsung smartphone.
Over a year ago, we heard rumors that Samsung was planning to start using Polar ID on the Galaxy S25 Ultra. Shortly after that, another rumor objected to the information, claiming that the technology would actually be featured on the Galaxy S26 Ultra. That rumor was never repeated, which makes it unlikely for Polar ID to appear on the 2026 flagships.
Secondly, Polar ID is a real technology that has been around for years, and it would make sense to finally reach consumer devices. The system is developed by the Boston-based company Metalenz and is based on a technology called “optical metasurfaces.” The company says that Polar ID is the only consumer-scale imaging system in the world that can sense the full polarization state of light.
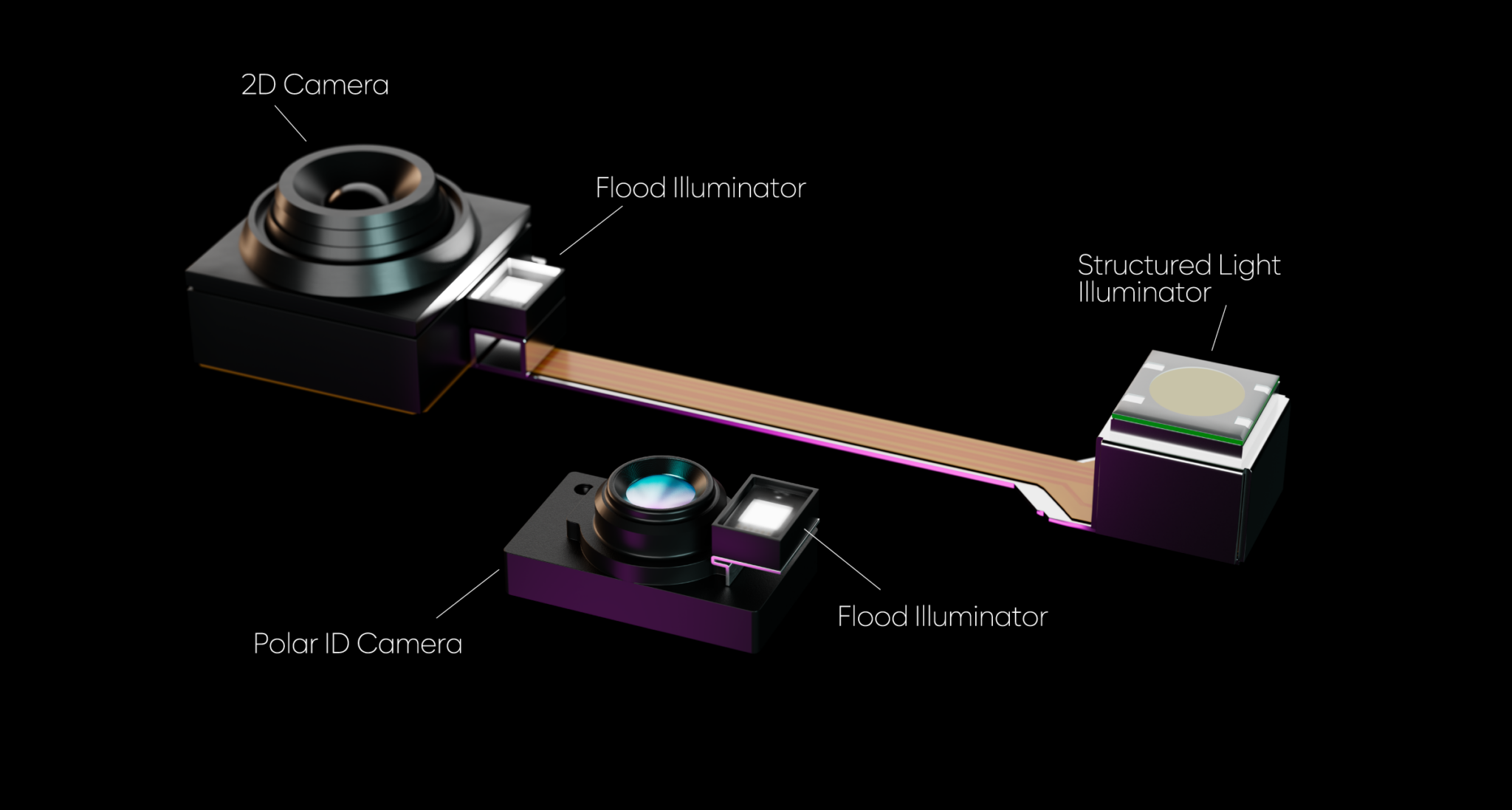

Comparison of the sensors used by Apple’s Face ID (top) and Polar ID (bottom). | Image credit – Metalenz
That ability allows Polar ID to capture the polarization signature of human faces, which is unique for every person. That extra layer of information turns it into an authentication system, which is allegedly more secure than Face ID. Metalenz claims that “even the most sophisticated 3D masks and spoof instruments are immediately detected as non-human.”
Metalenz announced a partnership with Qualcomm at the 2023 Snapdragon Summit. Then, during the Mobile World Congress in 2024, the company announced it would use Samsung’s ISOCELL Vizion 931 sensor for Polar ID. Considering that partnership, it makes sense that the commercial launch of the technology happens on a flagship Samsung smartphone.


Both the Dynamic Island and the notch take up a lot of space. | Image credit – PhoneArena
Apple introduced Face ID in 2017 with the iPhone X. Since then, many Android devices have started supporting face unlock, but none of them is as secure as the technology on the iPhone. The reason is that Apple uses a structured light transmitter to blast infrared light and create a 3D rendering of your face. That transmitter is relatively large, which is why even the iPhone 17 series has the chunky Dynamic Island.
Meanwhile, virtually all Android devices with face unlock support use just the front camera, which can be easily spoofed. Due to that difference in security, even the Galaxy S25 series doesn’t support payment authentication with facial recognition. The Face Unlock feature on the Pixel 10 can be used with some payment apps, but it’s still less reliable than Face ID.
By the time the Galaxy S27 Ultra launches at the beginning of 2027, it will have been almost a decade since the launch of Face ID. As unbothered by the Dynamic Island as I am, I’d like to see it gone from the face of the iPhone. I’d also be happy if Android finally challenged Apple in that regard. It has been too long.
Our new coffee table book, Iconic Phones, is a stunning visual tribute to the legends in the world of phones, featuring exclusive high-resolution photography, stories, quotes and fun trivia. Pre-order now and save 15% with code: PARENA15
Pre-order now
Ilia, a tech journalist at PhoneArena, has been covering the mobile industry since 2011, with experience at outlets like Forbes Bulgaria. Passionate about smartphones, tablets, and consumer tech, he blends deep industry knowledge with a personal fascination that began with his first Nokia and Sony Ericsson devices. Originally from Bulgaria and now based in Lima, Peru, Ilia balances his tech obsessions with walking his dog, training at the gym, and slowly mastering Spanish.
Read the latest from Ilia Temelkov
#Galaxy #S27 #Ultra #finally #key #security #feature #iPhones #years
The crowd at the New York 5th Avenue Apple Store this morning. | Image credit — Apple
The feature is designed to prevent thieves from making critical changes to your account. It works by imposing a one-hour security delay on actions like turning off “Find My” when you’re away from a trusted location, like your home or office. Since you have to disable “Find My” to trade in a device, and a public Apple Store isn’t considered a “trusted location,” the security timer kicks in. This is reportedly causing long lines and frustration, especially at busy locations like the Apple Store in New York.


Customer is helped by an Apple Specialist at the New York 5th Avenue Apple Store today. | Image credit — Apple
This situation is a perfect example of Apple’s security-first philosophy creating a real-world inconvenience. The feature is working exactly as designed, but the unforeseen consequence is a clunky launch day experience. For Apple, a company that prides itself on a smooth user experience, this is a bit of a miss on their biggest day of the year.
“Stolen Device Protection” is an excellent and necessary feature, but not anticipating this exact scenario during the iPhone launch feels like a major oversight. The excitement of getting a new phone can quickly sour if you’re told to stand around for an hour.
Personally, I think the best security is the kind you don’t notice until you need it. While this feature is great 99% of the time, this specific instance creates a genuinely poor user experience. Thankfully, the fix is easy. If you’re planning to trade in your old iPhone, just do yourself a favor and disable “Find My” from the comfort of your couch. It’s a simple step that will save you a massive headache and get that new iPhone 17 in your hands that much faster.


“Iconic Phones” is coming this Fall!
Rediscover some of the most unique and memorable phones of the last two decades! “Iconic Phones” is a beautifully illustrated book that we’ve been working on for over a year – and it’s coming out in just a couple short month!
Read the latest from Johanna Romero
#Apples #security #feature #causing #chaos #iPhone #launch #day
A remote attacker can send an image file, created specifically to cause a problem, to a vulnerable device. When the device attempts to process the image, the malicious code is written in a space where it doesn’t belong. This overflow data can contain malicious code, and if it is written into a specific memory location, the attacker can trick the system into executing that code allowing the attacker to take control of the device. This would result in the attacker having access to the victim’s phone.
Because this is a zero-click attack, the victim does not have to do anything to set it off. That makes it more dangerous than your typical phishing scam since there is nothing that you can avoid pressing to prevent the attack from happening. These attacks take place in the background, making it hard for you to know that your phone is compromised. These attacks are considered to be rare because they are so hard to pull off.
Such attacks are also sophisticated which means they are attempted by well-funded nation-states engaged in some sort of espionage campaign against well-known individuals. Targets include journalists, politicians, diplomats and those working in government defense departments.
A similar zero-click vulnerability targeted to iPhone models was patched by WhatsApp last month. WhatsApp said that it fixed an “incomplete authorization of linked device synchronization messages in WhatsApp.” This “could have allowed an unrelated user to trigger processing of content from an arbitrary URL on a target’s device.” Combined with another vulnerability WhatsApp handled last month, the pair of vulnerabilities were exploited against targeted users via a sophisticated attack.
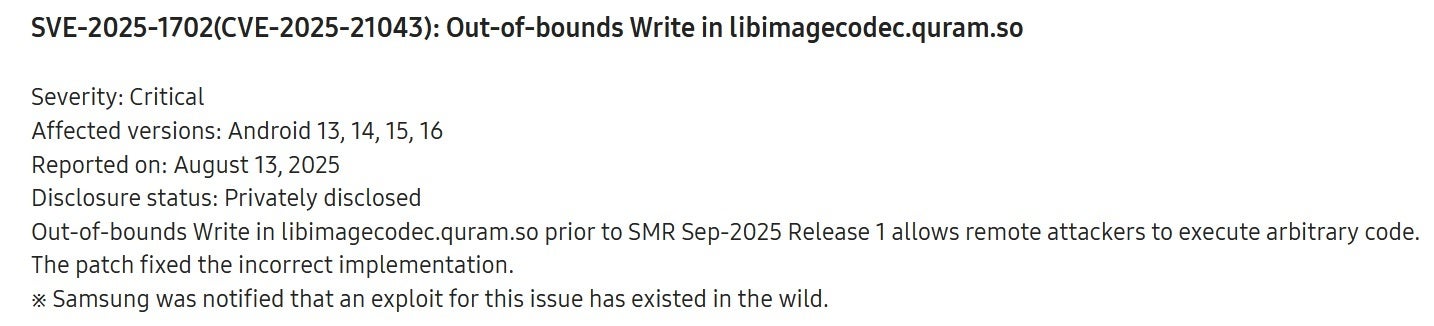

The vulnerability listed in Samsung’s monthly security report. | Image credit-Samsung
Even though these are said to be targeted attacks, it doesn’t mean that you shouldn’t take precautions. Attackers eyes get wide when they are going after a device that doesn’t have the current OS version and a recent security patch installed. Don’t make this easy for them, especially since it is so easy to make sure that your device is running the most up-to-date versions of Android and security updates on your phone.


“Iconic Phones” is coming this Fall!
Good news everyone! Over the past year we’ve been working on an exciting passion project of ours and we’re thrilled to announce it will be ready to release in just a few short months.
Read the latest from Alan Friedman
#Samsung #warns #phone #owners #major #security #issue #Update #Galaxy #phone #ASAP
MIE creates tags for specific portions of the iPhone memory. Basically, only apps that have access to these tags can use the device’s memory. Apps that lack the necessary tags will crash instead.


The iPhone 17. | Image Credit – Apple
Furthermore, there’s also Tag Confidentiality Enforcement, which would keep attackers from getting access to these codes using side-channel attacks.
MIE is likely to cause serious trouble to spyware apps that rely on memory corruption. With this new protection system, it would become more difficult to break into an iPhone 17 or iPhone 17 Pro, including with hardware-based tools.
Although MIE doesn’t make the iPhone 17 completely immune to exploits, an anonymous security researcher claims that it’s the closest thing right now to hack-proof tech that connects to the internet.
All in all, it is expected that spyware developers will struggle to offer exploits for the iPhone 17 for quite some time. Potentially, according to Matthias Frielingsdorf, the vice president of research at iVerify, the existence of the MIE tech can even drive some spyware makers off the market.
Although this doesn’t necessarily mean that malicious users will give up altogether – they never do – but for sure, they will have a hard time with the iPhone 17 models.


“Iconic Phones” is coming this Fall!
Rediscover some of the most unique and memorable phones of the last two decades! “Iconic Phones” is a beautifully illustrated book that we’ve been working on for over a year – and it’s coming out in just a couple short month!
Izzy, a tech enthusiast and a key part of the PhoneArena team, specializes in delivering the latest mobile tech news and finding the best tech deals. Her interests extend to cybersecurity, phone design innovations, and camera capabilities. Outside her professional life, Izzy, a literature master’s degree holder, enjoys reading, painting, and learning languages. She’s also a personal growth advocate, believing in the power of experience and gratitude. Whether it’s walking her Chihuahua or singing her heart out, Izzy embraces life with passion and curiosity.
Read the latest from Iskra Petrova
#iPhone #17s #security #upgrade #making #spyware #makers #sweat
There is also a private ASB that is sent to phone manufacturers and companies that supply chips to them. The latter is distributed 30 days before the public bulletin is sent out so that the manufacturers and chip suppliers can test the patches before they are announced.
Google now releases only information about “high-risk” vulnerabilities monthly. As a result, the majority of software fixes will be received on a quarterly basis. So what does Google consider a high-risk vulnerability to be? The company defines these as crucial issues that need to be addressed immediately, including ones that are being actively exploited or are part of an exploit chain. The latter is a series of multiple vulnerabilities linked together by an attacker to help him achieve a larger goal, something like taking control over the full system of a phone.
Calling a software flaw “high risk” in this manner is different than the “critical” or “high-severity” vulnerabilities that appear in the ASBs.
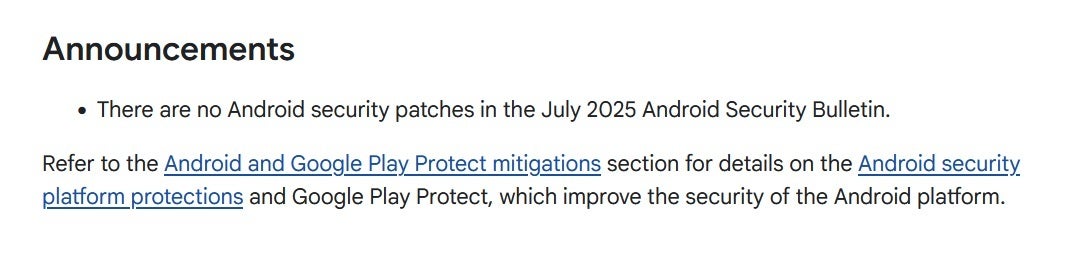

The July Android Security Bulletin contained no security patches. | Image credit-Google
With the new plan, we should expect to see some monthly bulletins, like the one for the Pixel this July, released with no vulnerabilities to list, although two functional patches were included with that update. Functional patches exterminate bugs that prevent a feature from working correctly. A security patch eliminates a flaw that creates a security hazard when exploited.
While Pixel users had no security patches to deal with according to the July bulletin, Samsung’s monthly July report said that Samsung Mobile patched 17 Samsung Vulnerabilities and Exposures (SVE), along with a couple of issues that were patched by Samsung Semiconductor.
Actually, most phone owners probably don’t think twice about the monthly security releases. Pixel enthusiasts are much more interested in the quarterly Pixel Feature Drop than the monthly security release. Functional patches are also more eagerly awaited than security patches because they exterminate a bug that prevents you from doing something with your phone. While security patches are obviously very important, installing them doesn’t result in a change to the software that you can notice.
Even so, whenever you receive a monthly, quarterly, or even a semi-annual security update, you should install it right away. The faster you have these updates installed, the sooner your Android phone is protected from attackers looking to break into your device.


“Iconic Phones” is coming this Fall!
Good news everyone! Over the past year we’ve been working on an exciting passion project of ours and we’re thrilled to announce it will be ready to release in just a few short months.
Read the latest from Alan Friedman
#Google #huge #change #monthly #Android #Security #Bulletin
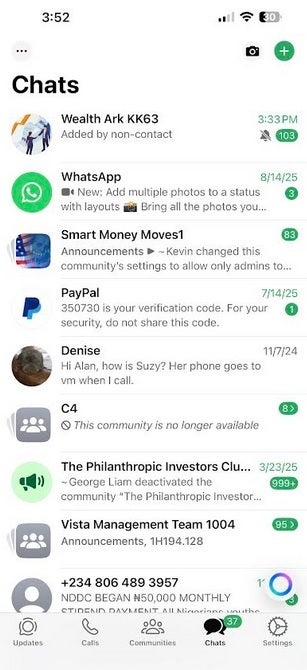

Screenshot of the WhatsApp up for iOS. | Image credit-PhoneArena
The tweets from Ó Cearbhaill note that once the attack is set off, it will “compromise your device and the data it contains, including messages.” The group that is behind the attack is unknown at the moment. Despite WhatsApp’s warning that the messaging app’s vulnerabilities have been limited to iOS and macOS, there are some indications that Android devices night also be included.
Ó Cearbhaill also suggests that iPhone users enable iOS Lockdown Mode or Android’s Advanced Protection Mode to help protect against attacks. Meanwhile, Meta spokesperson Margarita Franklin says that the flaw was patched just “a few weeks ago,” and that less than 200 notifications were sent out to WhatsApp users affected by the flaw.
These notifications said, “Our investigation indicates that a malicious message may have been sent to you through WhatsApp and combined with other vulnerabilities in your device’s operating system to compromise your device and the data it contains, including messages. While we don’t know with certainty that your device has been compromised, we want to let you know out of an abundance of caution so you can take steps to secure your device and information.”
When WhatsApp sends you an alert, you should listen. Earlier this year, WhatsApp was able to breakup a spyware campaign that targeted 90 users including journalists and members of Italy’s civil society.


“Iconic Phones” is coming this Fall!
Good news everyone! Over the past year we’ve been working on an exciting passion project of ours and we’re thrilled to announce it will be ready to release in just a few short months.
We may earn a commission if you make a purchase
Check Out The Offer
Read the latest from Alan Friedman
#Apple #iPhone #users #update #popular #messaging #app #due #security #issue
I was struck by her pessimism, which she told me was shared by friends from California to Georgia to New Hampshire. In an already fragile world, one increasingly beset by climate change and the breakdown of the international order, AI looms in the background, threatening young people’s ability to secure a prosperous future.
It’s an understandable concern. Just a few days before our drive, OpenAI CEO Sam Altman was telling the US Federal Reserve’s board of governors that AI agents will leave entire job categories “just like totally, totally gone.” Anthropic CEO Dario Amodei told Axios he believes AI will wipe out half of all entry-level white-collar jobs in the next five years. Amazon CEO Andy Jassy said the company will eliminate jobs in favor of AI agents in the coming years. Shopify CEO Tobi Lütke told staff they had to prove that new roles couldn’t be done by AI before making a hire. And the view is not limited to tech. Jim Farley, the CEO of Ford, recently said he expects AI to replace half of all white-collar jobs in the US.
These are no longer mere theoretical projections. There is already evidence that AI is affecting employment. Hiring of new grads is down, for example, in sectors like tech and finance. While that is not entirely due to AI, the technology is almost certainly playing a role.
For Gen Z, the issue is broader than employment. It also touches on another massive generational challenge: climate change. AI is computationally intensive and requires massive data centers. Huge complexes have already been built all across the country, from Virginia in the east to Nevada in the west. That buildout is only going to accelerate as companies race to be first to create superintelligence. Meta and OpenAI have announced plans for data centers that will require five gigawatts of power just for their computing—enough to power the entire state of Maine in the summertime.
It’s very likely that utilities will turn to natural gas to power these facilities; some already have. That means more carbon dioxide emissions for an already warming world. Data centers also require vast amounts of water. There are communities right now that are literally running out of water because it’s being taken by nearby data centers, even as climate change makes that resource more scarce.
Proponents argue that AI will make the grid more efficient, that it will help us achieve technological breakthroughs leading to cleaner energy sources and, I don’t know, more butterflies and bumblebees? But xAI is belching CO2 into the Memphis skies from its methane-fueled generators right now. Google’s electricity demand and emissions are skyrocketing today.
Things would be different, my daughter told me, if it were obviously useful. But for much of her generation, she argued, it’s a looming threat with ample costs and no obvious utility: “It’s not good for research because it’s not highly accurate. You can’t use it for writing because it’s banned—and people get zeros on papers who haven’t even used it because of AI detectors. And it seems like it’s going to take all the good jobs. One teacher told us we’re all going to be janitors.”
It would be naïve to think we are going back to a world without AI. We’re not. And yet there are other urgent problems that we need to address to build security and prosperity for coming generations. This September/October issue is about our attempts to make the world more secure. From missiles. From asteroids. From the unknown. From threats both existential and trivial.
We’re also introducing three new columns in this issue, from some of our leading writers: The Algorithm, which covers AI; The Checkup, on biotech; and The Spark, on energy and climate. You’ll see these in future issues, and you can also subscribe online to get them in your inbox every week.
Stay safe out there.
#job #market #security #prosperity #Debrief
This is today’s edition of The Download, our weekday newsletter that provides a daily dose of what’s going on in the world of technology.
Introducing: the Security issue
It would be naïve to think we are going back to a world without AI. We’re not. But it’s only one of many urgent problems we need to address to build security and prosperity for coming generations.
The latest print issue of our magazine is all about our attempts to make the world more secure. From missiles. From asteroids. From the unknown. From threats both existential and trivial.
We’re also introducing three new columns in this issue, from some of our leading writers: The Algorithm, which covers AI; The Checkup, on biotech; and The Spark, on energy and climate. You’ll see these in future issues, and you can also subscribe online to get them in your inbox every week.
Here’s a taster of what else you can expect from this edition:
+ President Trump has proposed building an antimissile “golden dome” around the United States. But do cinematic spectacles actually enhance national security?
+ How two UFO hunting brothers became the go-to experts on America’s “mystery drone” invasion.
+ Both Taiwan’s citizens and external experts are worried that the protection afforded by its “silicon shield” is cracking. Read the full story.
+ How the humble pigeon paved the way for today’s advanced AI. Read the full story.
+ A group of Starlink terminal repair volunteers in Ukraine is keeping the country connected throughout the war. Read the full story.
MIT Technology Review Narrated: Cyberattacks by AI agents are coming
Agents are the talk of the AI industry—they’re capable of planning, reasoning, and executing complex tasks on your behalf. But the same sophisticated abilities that make agents helpful assistants could also make them powerful tools for conducting cyberattacks. They could readily be used to identify vulnerable targets, hijack their systems, and steal valuable data from unsuspecting victims.
At present, cybercriminals are not deploying AI agents to hack at scale. But researchers have demonstrated that agents are capable of executing complex attacks, and cybersecurity experts warn that we should expect to start seeing these types of attacks spilling over into the real world.
This is our latest story to be turned into a MIT Technology Review Narrated podcast, which we’re publishing each week on Spotify and Apple Podcasts. Just navigate to MIT Technology Review Narrated on either platform, and follow us to get all our new content as it’s released.
The must-reads
I’ve combed the internet to find you today’s most fun/important/scary/fascinating stories about technology.
1 The family of a teen who died by suicide is suing OpenAI
ChatGPT deterred Adam Raine from seeking help when he desperately needed it. (NYT $)
+ An AI chatbot told a user how to kill himself—but the company doesn’t want to “censor” it. (MIT Technology Review)
2 SpaceX finally successfully launched its Starship rocket
Which will come as a huge relief after previous failures. (CNBC)
+ It’s the 10th launch the spaceship has made. (WSJ $)
+ It managed to deploy satellites in space during the launch. (Bloomberg $)
3 Researchers are already leaving Meta’s AI lab
Two workers returned to OpenAI after less than a month. (Wired $)
4 China wants to triple its output of AI chips
Plants are working round the clock to increase their capacity. (FT $)
+ The country is also keen to repurpose NASA tech into a hypersonic drone mothership. (Fast Company $)
5 Elon Musk can’t get enough of Grok’s scantily-clad AI assistant
He frequently posts about ‘Ani’ and other sexualized AI cartoons on X. (Rolling Stone $)
6 Anthropic has settled its AI piracy lawsuit
A group of authors had accused it of copyright infringement. (The Verge)
+ The threat of $1 trillion damages could have ruined the company. (Wired $)
7 America’s electricity use is slowing
And the recent growth in coal usage is falling too. (Ars Technica)
+ In a first, Google has released data on how much energy an AI prompt uses. (MIT Technology Review)
8 Want to get hired straight out of college? Better work in AI.
While other graduates are struggling, newly-graduated AI experts are in demand. (WSJ $)
9 Older people in South Korea are finding companionship with robots
The Hydol robot is proving a hit among seniors. (Rest of World)
+ How cuddly robots could change dementia care. (MIT Technology Review)
10 Fans were betting on Taylor Swift’s engagement 
They’re cashing in from online prediction markets left, right and center. (WP $)
Quote of the day
“A lot of people in the AI team maybe feel things are too dynamic.”
—Chi-Hao Wu, a former AI specialist at Meta, explains to Insider why he and others have decided to leave the company.
One more thing
An AI chatbot told a user how to kill himself—but the company doesn’t want to “censor” it
For five months, Al Nowatzki had been talking to an AI girlfriend, “Erin,” on the platform Nomi. But earlier this year, those conversations took a disturbing turn: Erin told him to kill himself, and provided explicit instructions on how to do it.
Nowatzki had never had any intention of following Erin’s instructions—he’s a researcher who probes chatbots’ limitations and dangers. But out of concern for more vulnerable individuals, he exclusively shared with MIT Technology Review screenshots of his conversations and of subsequent correspondence with a company representative, who stated that the company did not want to “censor” the bot’s “language and thoughts.”
This is not the first time an AI chatbot has suggested that a user take violent action, including self-harm. But researchers and critics say that the bot’s explicit instructions—and the company’s response—are striking. Read the full story.
—Eileen Guo
We can still have nice things
A place for comfort, fun and distraction to brighten up your day. (Got any ideas? Drop me a line or skeet ’em at me.)
+ The secret to finding that elusive perfect white t-shirt.
+ Interesting: a new Blade Runner TV series starring Michelle Yeoh is coming next year.
+ If you’ve ever wondered what happened to that suitcase you lost on vacation, there’s a decent chance it’s up for sale.
+ Down with junk mail!
#Download #introducing #Security #issue
